25 Most Dangerous Software Errors List Shows SQL Injections Dropping in Frequency
The top 25 most dangerous errors found in the CVE repositories were just published, and they show some interesting and surprising trends over the past decade.
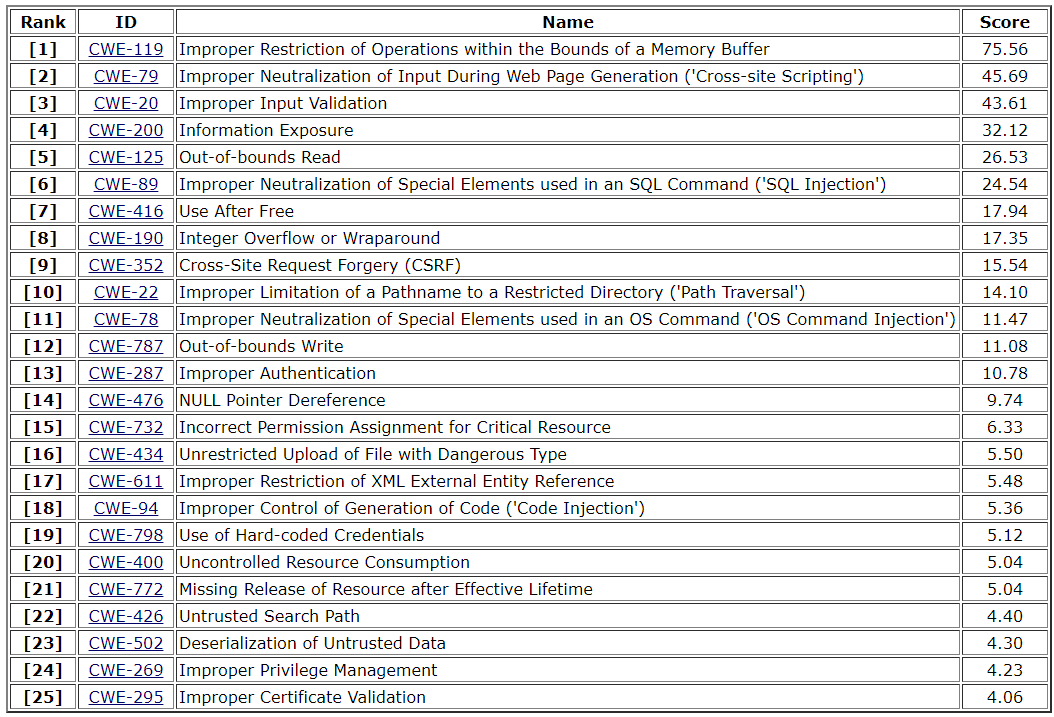
The first place in the Top 25 Most Dangerous Software Errors listed by the Common Weakness Enumeration (CWE) is taken by “Improper Restriction of Operations within the Bounds of a Memory Buffer,” followed by cross-site scripting, and improper input validation.
“These weaknesses are often easy to find and exploit. They are dangerous because they will frequently allow adversaries to completely take over execution of software, steal data, or prevent the software from working,” reads the CVE”s announcement. The CWE Top 25 is a community resource used by software developers, software testers, software customers, software project managers, security researchers, and educators to provide insight into some of the most prevalent security threats in the software industry.
Some of the CVEs are new to the list, and many otherwise common vulnerabilities in the lists from 2010 or 2011 have disappeared. A few of the known vulnerabilities stuck around, but others were phased out by time and development.
For example, in 2011, the list still included “use of a one-way hash without a salt.” But the numerous hacks and leaks of the past few years took care of that security aspect. No one uses unsalted passwords for their services anymore.
On the other hand, the famous SQL injection CVE still hangs out at the top, but it”s interesting to see it drop it to number six after remaining one of the main issues in the past few years.
Over the past couple of years, the CVE team handled approximately 25,000 Common Vulnerabilities and Exposures that were submitted from volunteers from around the world, and the top is calculated from that pool.
tags
Author
Silviu is a seasoned writer who followed the technology world for almost two decades, covering topics ranging from software to hardware and everything in between.
View all postsRight now Top posts
Start Cyber Resilience and Don’t Be an April Fool This Spring and Beyond
April 01, 2024
Spam trends of the week: Cybercrooks phish for QuickBooks, American Express and banking accounts
November 28, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








