Apple fixes flaw that displayed actual password rather than password hint
If you’re running macOS High Sierra on your desktop or laptop, stop right now and make sure you have applied the latest security update.
Yesterday, Apple released a free supplemental update to macOS High Sierra 10.13 – just over one week since the general release of the operating system.
As an Apple support knowledgebase article explains, macOS High Sierra shipped with a potentially disastrous security hole in its Disk Utility tool that could have allowed anyone to access encrypted Apple File System (APFS) volumes.
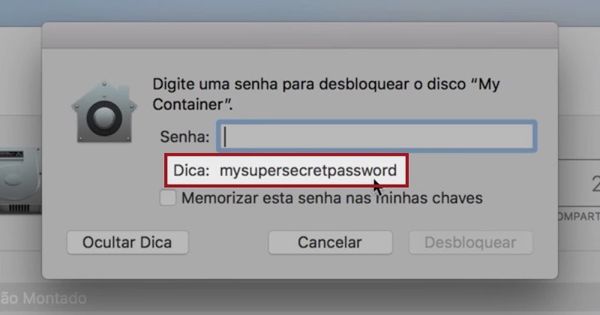
As Brazilian developer Matheus Mariano discovered , a bug in the operating system’s code meant that clicking on the “Show Hint” button when attempting to access an encrypted volume would *not* display the password hint as you would expect.
Instead, it would display the actual plaintext password for the volume.
In short, if you don’t know the password don’t panic. Just hit the password hint button and the operating system will tell you.
Mariano demonstrated the security flaw in a YouTube video:
According to Apple, the password can be displayed instead of the password hint if you use Disk Utility to add an encrypted APFS Volume, and you supplied a password hint.
Fortunately, the new supplemental update patches macOS High Sierra 10.13 – as well as against other bugs, including a zero-day flaw that could allow a malicious attacker to steal passwords from the Keychain.
The update can be easily downloaded and applied using the Software Update functionality within the Mac App Store.
In its knowledgebase article, Apple recommends that after updating macOS High Sierra you go through a process to erase and recreate affected encrypted APFS volumes
To its credit, Apple issued a fix for the password-revealing bug very quickly, and its responsiveness in addressing this issue should be applauded. However, that doesn’t change the fact that such a serious bug like this really should have been intercepted during its quality control process, rather than allowed to ship to millions of computers around the world.
tags
Author
Graham Cluley is an award-winning security blogger, researcher and public speaker. He has been working in the computer security industry since the early 1990s.
View all postsRight now Top posts
Start Cyber Resilience and Don’t Be an April Fool This Spring and Beyond
April 01, 2024
Spam trends of the week: Cybercrooks phish for QuickBooks, American Express and banking accounts
November 28, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks









