Black Hat 2017: Researcher shows how phishing scams are getting so good they can even trick techies
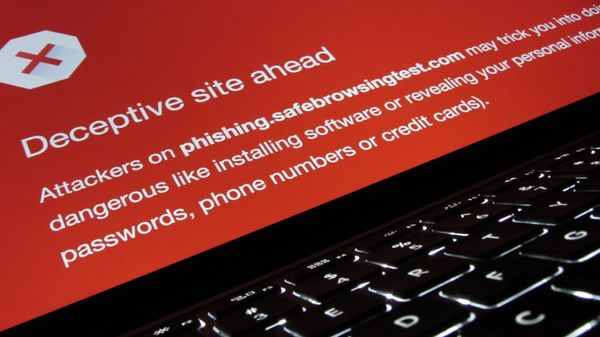
Security experts agree that a sure-fire way to get your data compromised is to not train your staff in cybersecurity. However, as one researcher showed at Black Hat 2017, even solid training may not thwart the newest phishing scams.
We also need hardcoded solutions against today”s email and website spoofing, according to Karla Burnett, security engineer at mobile payment company Stripe.
In a Black Hat presentation titled “Ichthyology,” Burnett demonstrated how even her colleagues – who helped her set up rigged sites as part of a test – fell victim to their own phishing experiment.
How? The answer to this question, Burnett believes, can be found in Daniel Kahneman’s book “Thinking, Fast and Slow.” The book explains how the human brain uses two modes of thinking when faced with decisions: System 1 is instinctive, and System 2 is more methodical and calculated.
Burnett argues that with the huge influx of emails to our inbox every day, it”s impossible to apply System 2 to every single message. Couple this with the fact that phishing sites now include “trailouts” (redirects to the original site they are impersonating) and you can trick even technical users into handing over their credentials.
“People who know what they’re doing fall for this stuff,” she said.
While two factor authentication (2FA) is good, it does little to protect users against phishing, according to the researcher. SMS is just one example of a flawed system that renders 2FA nearly useless in a phishing attack.
Burnett advocates a technical solution. She proposed SSL client certificates for authenticating the domain making the request.
“The server requests a certificate, and the user’s machine serves it up,” she said. “They’re kind of like cookies but without all the downsides of cookies. They’re not a single shared secret being passed around everywhere.”
U2F (Universal 2nd Factor) would also work well, as it generates a unique credential for each domain every time that domain requires authentication.
“The underlying issue here is that any protection that relies on a human being making a reasonable decision is going to fail. We need to find technical solutions to this problem rather than just say, ‘We’ll train people and everything will be fine’,” Burnett concluded.
In the first three months of 2016, spam email containing attached files increased 50% from a year earlier, data from Bitdefender”s Antispam Lab revealed. Around the same time, spammers stepped up their use of new clever tactics like whaling and spear-phishing.
Locky and Petya, two emerging ransomware threats, were largely responsible for the uptick. Ransomware accounted for 15.5% of all measured e-mail antivirus detections last year. In other words, one in seven malicious email attachments delivered in Q1 2016 contained some form of ransomware.
tags
Author
Filip has 15 years of experience in technology journalism. In recent years, he has turned his focus to cybersecurity in his role as Information Security Analyst at Bitdefender.
View all postsRight now Top posts
Start Cyber Resilience and Don’t Be an April Fool This Spring and Beyond
April 01, 2024
Spam trends of the week: Cybercrooks phish for QuickBooks, American Express and banking accounts
November 28, 2023
3 in 5 travel-themed spam emails are scams, Bitdefender Antispam Lab warns
August 10, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








