CryptoWall 4.0 returns to the wild, posing as good guy
The infamous CryptoWall ransomware family is back, encrypting files under the false pretenses of testing AV solutions for their “suitability” to protect data.
“CryptoWall Project is not malicious and is not intended to harm a person and his/her information data. The project is conducted for the sole purpose of instruction in the field of information security, as well as certification of antivirus products for their suitability for data protection. Together we make the Internet a better and safer place.”
This time, users are requested to pay $700 worth of Bitcoins (1.83 BTC). CryptoWall, active since April 2014 under three known versions, has inflicted more than $1 million in losses every month, according to federal reports.
Bitdefender malware researchers analyzed a sample of the fresh strain of malware and saw clear differences between CryptoWall 4.0 and its predecessors.
In terms of propagation, CryptoWall seems to employ the same e-mail distribution methods as before, via infected emails.
Fig 1. CryptoWall-infected spam email
The malware displays a redesigned ransom message and new filenames, but the most notable change is that CryptoWall 4.0 now encodes the names of the files. The name of each file is changed into a random string of characters, while the original name of the file is written inside it. The entire file gets encrypted. This makes recognizing the files almost impossible, much to the frustration of users.
Fig. 2 Documents prior to CryptoWall 4.0 infection
Fig 3. Documents after CryptoWall 4.0 encryption
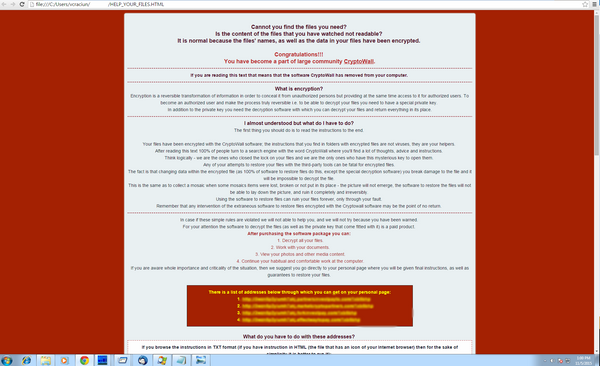
After it installs and encrypts files, the malware displays a ransom note in three formats: HTML, TXT and PNG. The message is noticeably different for previous versions: longer, less alarming and with a hint of irony.
Fig 4. HTML ransom note after infection
After educating users on encryption, hackers also make it clear they are the sole owners of the so-called decryption software users are urged to pay for and “any attempts to restore your files with the third-party tools can be fatal for encrypted files.” Metaphorically put, the damaged files are like missing puzzle pieces, the picture will never be complete again.
To preserve anonymity, the ransomware asks users to pay the ransom via a Tor address. The attackers also warn users that AV solutions are “to blame” if instructions are deleted, namely blocking the virus. In this case, they’ve laid down a plan B – another set of instructions on how to install Tor.
The message recommends that the payment be completed in 2-3 days, in case of a takedown of the links.
CryptoWall 4.0 continues to utilize the same Decrypt Service site as previous versions. From this site a victim can make payments, find out the status of a payment, get one free decryption, and create support requests.
Fig. 5 Decrypt service payment site
The encryption standards employed seem to remain the same – RSA-2048 – a strong encryption algorithm that renders decryption impossible.
Bitdefender’s investigation is ongoing and further details will be disclosed soon. Technical information is provided courtesy of Bitdefender’s anti-malware experts Dragos Gavrilut, Razvan Benchea and Cristina Vatamanu.
tags
Author
Alexandra started writing about IT at the dawn of the decade - when an iPad was an eye-injury patch, we were minus Google+ and we all had Jobs.
View all postsRight now Top posts
Start Cyber Resilience and Don’t Be an April Fool This Spring and Beyond
April 01, 2024
Spam trends of the week: Cybercrooks phish for QuickBooks, American Express and banking accounts
November 28, 2023
3 in 5 travel-themed spam emails are scams, Bitdefender Antispam Lab warns
August 10, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks













