Fake AV Uses Stolen Digital Certificate to Evade Detection
Malware creators, who first started pumping out fake antivirus solutions in 2008, are now taking them to the next level by tinkering with user trust. Bitdefender just stumbled on a number of samples for a product called Antivirus Security Pro, a sub-species of fake antivirus that comes with a digitally-signed installer to circumvent some security mechanisms of the operating system and antivirus solution.
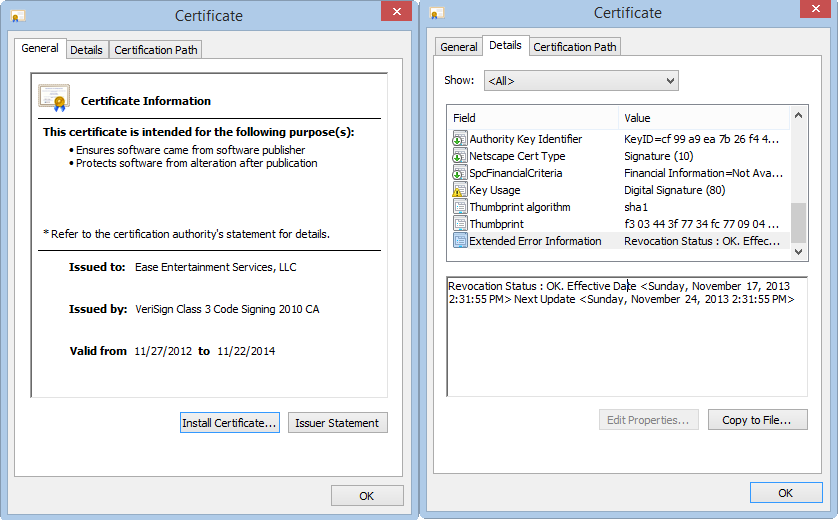
More to the point, the installer file served via the Internet is signed with a digital certificate issued for Ease Entertainment Services, LLC on November 22nd last year. The digital certificate is still valid (it has not been revoked yet). Most likely, it was stolen.
Although the digital certificate is still valid for roughly one year (it would have naturally expired on November 22nd 2014), cyber-criminals did not time-stamp it to extend its validity, most likely because they know the private key will be revoked soon. Stolen digital certificates are a business by themselves, but due to the sensitive nature of such a compromise, they are usually revoked very quickly.
This is not the only family of Fake AV that has been abusing stolen digital certificates lately: earlier this month, the WinWebSec rogue antivirus abused the digital certificate issued for Ingenieursbureau Matrix B.V. The certificate was quickly revoked after misuse was identified, but hundreds digitally-signed pieces of malware were already in the wild.
Why is the digital signature so important?
Digitally-signed applications ensure (or should ensure) the integrity and trustworthiness of the respective code. Digitally-signed files come from known vendors scrutinized in advance and deemed trustworthy by certification authorities. This is why some antivirus solutions still skip digitally signed files to improve scanning performance.
Also, modern operating systems treat digitally signed files differently when they attempt to perform system-wide modifications. Prompts of unsigned applications trying to elevate their privileges attract much more user scrutiny than other prompts.
Digitally-signed application (left) and a regular executable (right) trying to elevate to administrator. The UAC prompts look different.
We have notified the affected entity about the breach and provided them with further information to revoke the compromised certificate. In the meantime, make sure that you only download files from sources you trust, regardless of whether they are signed or not.
Article courtesy to Adrian Popescu, Bitdefender malware researcher.
tags
Author

Bogdan is living his second childhood at Bitdefender as director of threat research.
View all postsRight now Top posts
Start Cyber Resilience and Don’t Be an April Fool This Spring and Beyond
April 01, 2024
Spam trends of the week: Cybercrooks phish for QuickBooks, American Express and banking accounts
November 28, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks










