First Ransomware Disguised as Windows 10 Upgrade, Bitdefender Warns
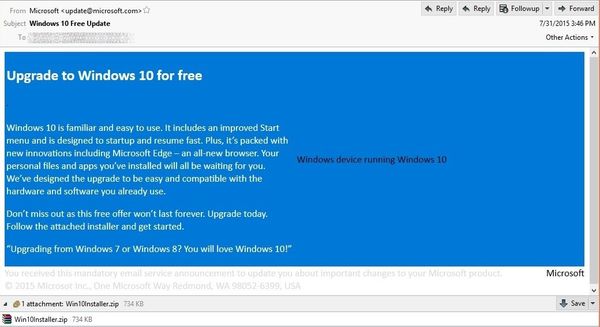
Don’t be fooled by fake emails offering updates to operating systems and other software! Cyber-extortionists are trying to take advantage of the millions of people looking for a free system upgrade to Windows 10.
Cybercriminals are spreading CTB Locker via fake emails claiming to install Windows 10 kits, Bitdefender Antispam Labs found. Attackers demand 2 Bitcoins (worth $600) be paid within 96 hours to restore the encrypted files.
Microsoft launched Windows 10 on July 29 and is rolling out the new version in waves to users around the world. In this context, an email claiming to come from the company can pique the interest of thousands of users.
The From field features the email address [email protected] which appears to be a valid, official address, while the subject line clearly states the supposed purpose of the email “Windows 10 Free Update.”
Disguised as an innocent Windows 10 installer, the ransomware needs to be downloaded and executed manually by the user. Once installation is complete, the victim sees this warning message:
Infected users are instructed to pay $600 for the private key stored on their servers – without it, decryption is impossible. When the ransom is paid, decryption will start and a payment verification screen will be displayed.
CTB Locker is a file-encryptor, the successor of Cryptolocker. Despite successive short-lived take downs, Cryptolocker has managed to make a comeback through this newer version. This challenging breed of malware is constantly evolving, becoming more dangerous and reaching new levels of complexity.
“This software release creates the perfect context for cybercriminals and they’re fully taking advantage of it,” said Bogdan Botezatu, Senior E-Threat Analyst at Bitdefender. “Millions of people are expected to upgrade to Windows 10, so we might witness a substantial number of PC users falling victim to such scams.”
According to Bitdefender Labs, the malicious emails were sent in three days from spam servers located in Russia, the US, Thailand, Ukraine, India, Kazakhstan, Taiwan and France.
Bitdefender, which detects and blocks the threat, advises users to install software updates only from reputable sites and reminds them to avoid accessing attachments and links from unrequested emails.
This article is based on the technical information provided courtesy of Bitdefender Senior Antispam Researcher Adrian MIRON.
tags
Author
Alexandra started writing about IT at the dawn of the decade - when an iPad was an eye-injury patch, we were minus Google+ and we all had Jobs.
View all postsRight now Top posts
Start Cyber Resilience and Don’t Be an April Fool This Spring and Beyond
April 01, 2024
Spam trends of the week: Cybercrooks phish for QuickBooks, American Express and banking accounts
November 28, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks










