Google's CEO Sundar Pichai hit by hackers
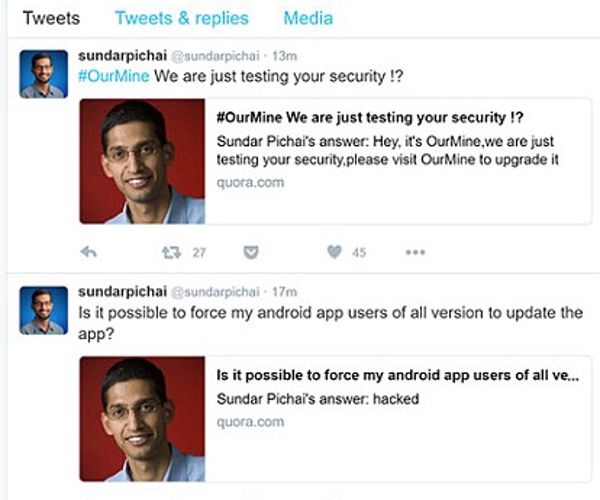
The hacking group which broke into social media accounts of Facebook CEO Mark Zuckerberg have claimed another high profile scalp: the CEO of Google.
Source: Twitter
As Softpedia reports, the OurMine hacking gang broke into the Quora account of Google CEO Sundar Pichai this weekend.
The Quora question-and-answer site probably isn’t the most high profile account owned by Pichai, but unfortunately for him he had connected the site to his Twitter account.
Which meant that the hackers could cross-post messages from Quora to the Google CEO’s Twitter page, where they would be seen by his over half-a-million followers.
Is it possible to force my android app uses of all version to update the app?
Sundar Pichai’s answer: hacked
Fortunately the hackers did not use the opportunity to spam out malicious links which might have infected the computers of the Google CEO’s followers or attempted to phish login credentials from them. Instead, it appears that the OurMine gang were more interested in showing off what they had managed to do.
The OurMine hacking group told The Next Web that it had exploited a vulnerability in Quora’s platform to access Pichai’s account, and that it wanted to raise awareness before other hackers took advantage:
“We are just testing people security (sic), we never change their passwords, we did it because there is other hackers can hack them and change everything.”
Whether it is true that Quora has a vulnerability or not is uncertain. After all, we only have the hackers’ word for it.
Another possibility is that Sundar Pichai made the (sadly not uncommon) mistake of using the same password for his Quora account as one he was using on one of the sites (LinkedIn? Tumblr? MySpace?) that has recently been found to have suffered a mega-breach.
So, what can we learn from this?
Firstly, no-one is immune from making poor decisions when it comes to protecting their online accounts. Sundar Pichai is – compared to most people – as nerdy as they get, and yet he still became unravelled because of poor security decisions. Most likely the error he made was using the same password in multiple places – a big no no.
Secondly, having a strong unique password on your Twitter account and even two-step verification is not necessarily a guarantee that an unauthorised party cannot post to your Twitter page without your permission. You should be cautious about what sites and applications you connect to your Twitter account, and be wary of allowing third-party sites to auto-tweet on your behalf.
Thirdly, whenever a site you use suffers from a security breach follow their advice regarding changing your passwords and enabling additional security features when available. Security doesn’t just matter at the sites that you use frequently, but also at ones you may have used years before and have perhaps largely forgotten about.
The tighter you batten down your hatches, the less opportunities you give for data to leak.
tags
Author
Graham Cluley is an award-winning security blogger, researcher and public speaker. He has been working in the computer security industry since the early 1990s.
View all postsRight now Top posts
Start Cyber Resilience and Don’t Be an April Fool This Spring and Beyond
April 01, 2024
Spam trends of the week: Cybercrooks phish for QuickBooks, American Express and banking accounts
November 28, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks










