Internet Explorer bug can reveal the contents of your address bar
If you’re one of the many people still using Microsoft Internet Explorer to surf the internet, you have just been given another good reason to upgrade to a more modern browser.
Independent security researcher Manuel Caballero has revealed an unpatched vulnerability in Internet Explorer that could allow a malicious attacker to capture sensitive information that you would never intentionally share with a website you are visiting – such as where you plan to visit next on the internet, or what terms you might be searching for on the internet.
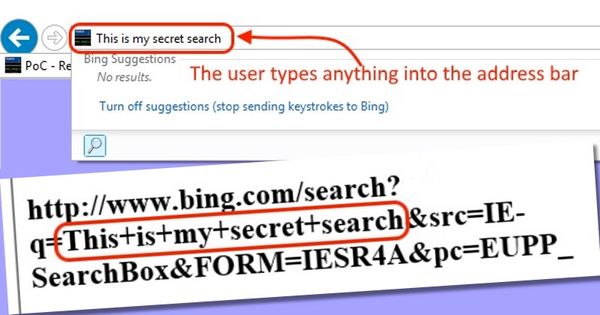
The vulnerability reveals the sensitive information by allowing a snooping website to snoop on the Internet Explorer browser’s address bar, capturing whatever you have typed there as soon as you press the enter key.
Caballero explains in a blog post how the privacy-busting vulnerability is exploited:
“When a script is executed inside an object-html tag, the location object will get confused and return the main location instead of its own. To be precise, it will return the text written in the address bar so whatever the user types there will be accessible by the attacker.”
The security hole is present in the latest version of Internet Explorer, but does not affect users of other browsers including Microsoft Edge which ships with new installations of Windows 10.
Caballero has published a YouTube video demonstrating how the flaw can be exploited.
In the video of Caballero’s proof-of-concept demonstration it is visually apparent to the user that the information they entered into the address bar is being grabbed by the malicious webpage. However, the researcher says that the code can be adapted to steal information entirely surreptitiously.
If you were still waiting for a reason to switch to a more modern browser like Chrome, Edge, or Firefox, then this could well be it.
Although there are no reports of anyone maliciously exploiting the vulnerability in the wild, the fact that Caballero has published proof-of-concept code means that there may be no end of opportunistic cybercriminals who will seek to adapt the exploit to silently spy on unsuspecting Internet Explorer users.
tags
Author
Graham Cluley is an award-winning security blogger, researcher and public speaker. He has been working in the computer security industry since the early 1990s.
View all postsRight now Top posts
Start Cyber Resilience and Don’t Be an April Fool This Spring and Beyond
April 01, 2024
Spam trends of the week: Cybercrooks phish for QuickBooks, American Express and banking accounts
November 28, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








