MacOS High Sierra Security Flaw Allows Root Access with No Password
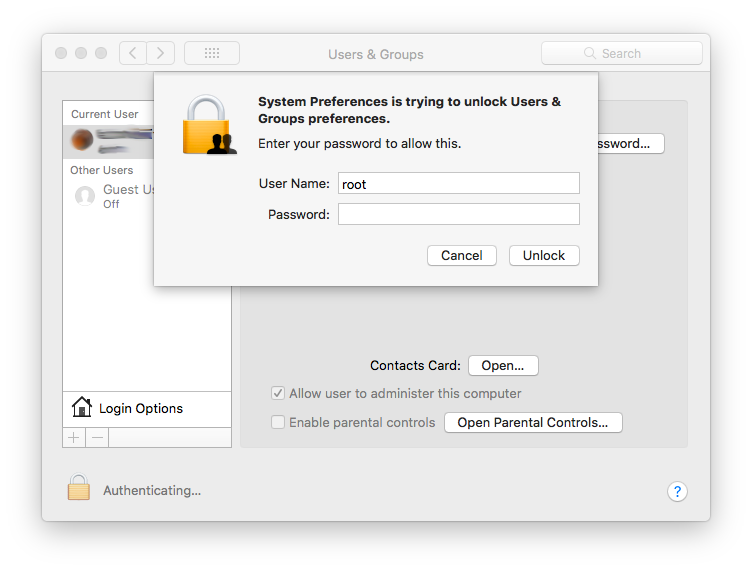
A recent security flaw in Apple”s latest MacOS distribution, High Sierra, enables anyone to log in as “root” – the highest level of administrative privileges – without using a password for authentication. The trivial vulnerability is present in macOS High Sierra 10.13.x, and everyone using these releases is technically affected.
Because MacOS is a Unix/Linux-based system, root access translates into full administrative privileges over the system, which means installing malware, removing apps, enabling or disabling security features, and pretty much everything in between. Since access to this administrative account is enabled with no password or authentication, this is considered a major security issue.
“You can access it via System Preferences>Users & Groups>Click the lock to make changes. Then use “root” with no password. And try it for several times. Result is unbelievable!,” wrote Lemi Orhan Ergin over Twitter, the one who first discovered the flaw.
Although the vulnerability seems to require attackers to have physical access to the machine, security analyst Will Dormann notes that MacOS has a “Screen Sharing” feature that would let anyone remotely connect to the machine using a graphical interface. Technically, that type of remote control would allow the attacker to log in as root and exploit the current vulnerability.
“The Apple High Sierra root issue is bad,” wrote Dormann over Twitter. “If you have exposed “Screen Sharing”, you can allow people into your machine with full GUI access, using no password.”
While there have been no reports in the wild of cyber criminals actively exploiting this security issue, everyone with macOS High Sierra 10.13.0 and above is encouraged to set strong password for their “root” account as soon as possible. Simply disabling the root account is not an option, as it would be re-enabled once the user logs into his account.
Locking down the “root” account with a strong password prevents local or remote ill-intended parties from tampering with your MacOS, which is why everyone is encouraged to do so immediately. For a couple of easy tips on how to create a strong password, check out our handy guide here.
While Apple has acknowledged the security issue, it seems that only the macOS High Sierra 10.13.2 beta seems to have received a fix. Since there”s no estimate when a patch will be available for everyone, the safest way to address the issue is to set your own root password. Now!
For more information on how to add a password to your “root” account, check out Apple’s Support page for details.
tags
Author
Liviu Arsene is the proud owner of the secret to the fountain of never-ending energy. That's what's been helping him work his everything off as a passionate tech news editor for the past few years.
View all postsRight now Top posts
Start Cyber Resilience and Don’t Be an April Fool This Spring and Beyond
April 01, 2024
Spam trends of the week: Cybercrooks phish for QuickBooks, American Express and banking accounts
November 28, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








