New Apple ID phishing attack targets your on- and off-line life
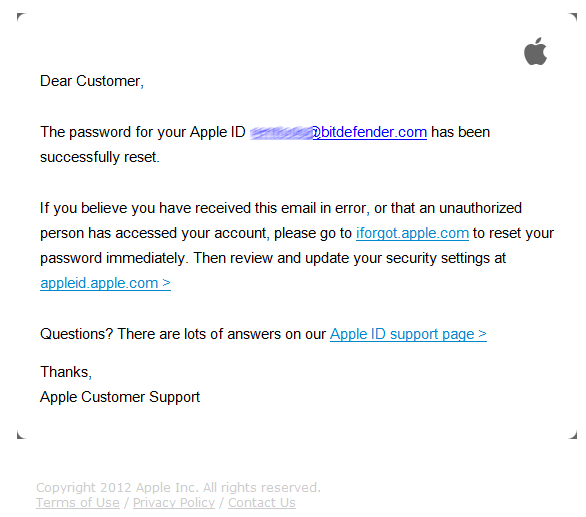
New phishing campaign that claims to safely change your Apple ID password is in fact fishing for gadget owners’ critical information.
Apple customers are once again the target of a phishing campaign that attempts to collect log-in information. The message, disguised as a password reset message, lures victims to a phishing web page to “review” the original password.
Making use of social engineering, the scammers trick users into willingly handing over identification data to their Apple accounts. Crooks included in the message body no fewer than three links towards Apple’s support pages – the one dedicated to those who forget their passwords to help them reset the password “if in doubt”, one to the questions and answers section and the third to the alleged Apple support page – AppleID – if the user wants to â”review and update security setting”Â.
These three links however lead the user to spoofed pages created by the crooks to collect account IDs and passwords from all users who might fall into the trap, willingly access it, and change their old passwords with new ones. The moment users type in their log in username and password on the fake login page, they will in fact hand the critical data to crooks.
The message is clean, to the point, and in perfectly correct and formal English and the simple signature “Apple Customer Support” will offer no clue about the scam.
Fig.1. Fake e-mail allegedly sent by Apple Customer Support Team
This Apple ID is for the Apple customer the virtual key that allows the attacker access not a service, but a series of services and option ” basically everything the Apple user would do with their computer: purchasing applications at the victim’s expense, access data in the iCloud and so on.
From the iCloud user account, someone can locate, wipe, lock the registered gadgets. Imagine how dangerous a crook with access to the user’s ICloud account can be: they can literally track the user as long as they have their IPad or Iphone on them. They can access users’ documents, both personal and work-related, since the iCloud is the default save location for all new created documents, presentations and spreadsheets. As a bonus, the attacker gets access to the e-mail account and contact list, that are also available from the iCloud for synchronization purposes.
You may wonder why this type of attacks works. Maybe because people know that security breaches happen quite often. Passwords and IDs are stolen and almost every month companies see themselves forced to ask their customers to change their passwords – or better yet – change the passwords immediately, then notify the user. The database breaches that affected Last.FM and LinkedIn, to mention only a few, give this kind of message credibility and context.
tags
Author
A blend of product manager and journalist with a pinch of e-threat analysis, Loredana writes mostly about malware and spam. She believes that most errors happen between the keyboard and the chair.
View all postsRight now Top posts
Start Cyber Resilience and Don’t Be an April Fool This Spring and Beyond
April 01, 2024
Spam trends of the week: Cybercrooks phish for QuickBooks, American Express and banking accounts
November 28, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks









