Penetrating and Achieving Persistence in Highly Secured Networks
Only a couple of years ago, cyber-criminals almost exclusively targeted Internet-connected end-users and companies. Now, high profile attacks target isolated, highly secure corporate or business environments. This paper describes the challenges of breaching such systems, achieving persistence for as long as possible and payload delivery mechanisms.
Ever since government and companies adopted the Internet on a massive scale, cyber-criminals have become interested in breaching these critical infrastructures and monetizing them in various ways, with particular focus on disruption and information theft.
The continuous siege from outside hostile parties has prompted businesses, enterprises, governments and mission-critical service companies such as utility providers to isolate their networks and render them inaccessible (or limit their accessibility) to the outside world. As a rule, the more critical the network is, the higher the degree of isolation.
How is successful penetration carried in isolated environments?
One of the most frequent mistakes when deploying a highly secure network is allowing it to be extended without the intervention of a network administrator. Many times, employees trade security for usability without even realizing they are exposing the network to outside threats. Wireless access points installed without notification and without proper security, public and private network bridging through proxy servers or the installation of other devices for tethering (i.e. mobile phones or 3G modems) can and will annihilate any safety mechanism the network administrator has in place.
An advanced persistent threat attack begins with either exploiting one of the technical vulnerabilities exposed above, or by social engineering the user into breaking security protocols of the organization, such as the restriction to plug in a USB drive in computers that are part of the private network. The goal of an advanced persistent threat is gaining prolonged access to an organization`s resources for monitoring or sabotage.
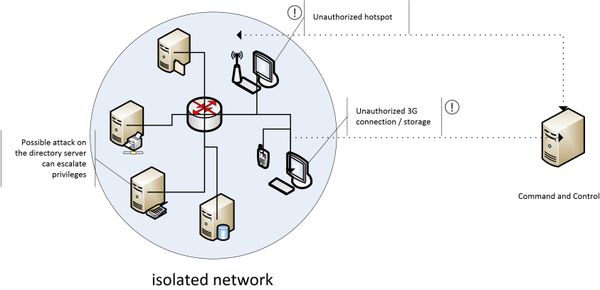
Figure 1: Vulnerable spots of a protected network. Wireless extensions and unauthorized gateways to the Internet expose the network to outside attackers.
Exploitation of an unauthorized extension of the network with wireless devices is the easiest method in which a cyber-criminal in close proximity can gain access to a protected environment. In the absence of a strong audit of the network configuration, legitimate users could add a wireless router in a spare Ethernet outlet or even bridge a wireless connection to work in access point mode. Most of the times, these are not deliberate acts of sabotage, but fatal mistakes aimed at enhancing usability of a restrictive networking environment (i.e. sharing the local internet connection with a smartphone or creating a wireless connection in the meeting room without consent from the network administrator). This way, any nearby attacker can probe the Wi-Fi space for unprotected or poorly-secured networks, then use open-source tools to attack WEP, WPA, LEAP or even VPNs and other proprietary wireless technologies[1]. Once the network has been identified, cracking the rudimentary encryption would allow the attacker to connect to the network to access resources.
Mitigation:
- As a system administrator, you should always disable any Ethernet outlet that is not in permanent use directly from the patch panel in the server room.
- Configure your DHCP server to lease IPs by MAC addresses only.
- Talk to employees about the importance of keeping the network isolated at all times. Make them understand that any modification to the network infrastructure will have disastrous effects.
- Use Wi-Fi space monitoring tools to detect wireless signals originating from your facility. A simple $10 key fob Wi-Fi signal detector is often enough to identify illegal access points in your organization
Unregulated access to the internet via 3G modems or 3G tethering defeats the purpose of isolating the network environment. Whenever the user connects to the internet through a personal device from a machine that is part of the isolated network, they become perfect targets for blended threats ” malware delivered via well formatted e-mail messages that trick the user into either downloading an infected and apparently innocuous attachment (such as a PDF or document file) or prompt the user to visit a legitimate website hosting malware.
Mitigation:
- Enforce security policies on all computers connected to the network. Disable or render USB ports physically inaccessible to prevent storage devices from connecting to the PC. This way, users can`t inadvertently plant malware and can`t move stolen information outside of the network.
- Block Bluetooth and wireless on host computers to disallow file transfers and interconnection with user-owned devices.
Personal storage and multimedia devices arbitrarily plugged into network computers can act as highly effective vectors not only for malware, but also for the information that escapes the network to the attacker`s command and control server. This approach, although less effective than directly sending data to the attacker via the Internet, has proven much more successful in high-profile attacks such as the Flamer incident[2].
Last, but not least, mind the physical security of the facility. Even the most secured networking environment is useless if physical access to the facility, data center or server room is lax or unregulated. Skilled social engineers can cut their way through office buildings; determined attackers can convince or coerce personnel with access to the building (employees, janitorial team, maintenance crew) to plant devices for them and open security breaches at the network perimeter. The Darpa-funded Pwnie Express products[3] for instance are disguised as power strips and can be connected to the network, then used by attackers for persistent access to the network over 3G.
Achieving persistence in isolated environments
For long-term exploitation of the isolated network, attackers use a combination of malware tools that take care of deployment, data and password gathering, scanning the network perimeter and reporting. These tools keep a low profile and are specially designed to evade antivirus detection. The evasion is possible because, most of the time, the cyber-criminal team behind the attack uses brand-new code that has never been seen in the wild by antivirus vendors. Zero-day exploitation against client software plays a key role in the stealthy dissemination of the payload across the network, aided by unconventional malware programming using less known APIs and next to no obfuscation of the malicious code.
A key advantage of an isolated environment is that it is considered clean and virus-free. By design, they allow no intrusion from the outside, as they are rarely connected to other networks. More than that, one of the most effective means of defense against malware is only partially functional: in the absence of a permanent connection to the internet to deliver hourly malware signature updates, the antivirus uses only outdated signatures and behavioral patterns ” two technologies that are highly ineffective against brand-new malicious code engineered to conceal suspicious behavior.
We know advanced malicious code used in breaching isolated networks often comes unencrypted, unpacked and needs no internet connection to operate. These features are critical in evading antivirus detection that monitors code changes, entropy and typical malicious behavior. This was the case of Flamer, the world`s largest piece of malware, which avoided detection by having the exact opposite features of modern, commercial malware. In the absence of an antivirus solution to flag the intrusion, it is up to the network administrator to mitigate a possible infection by constantly monitoring network traffic and ensuring that security policies are enforced.
Figure 2: The circuit of a Flamer-infected device: the employee is used both as a vector of infection and as a carrier for stolen data
Payload delivery and operation mechanism
One of the most frequently-encountered misconceptions is that a piece of malware is only harmful when it can actively communicate with the command and control server. While this is mostly true for consumer-grade malware that specializes in sending spam, harvesting addresses or manipulating banking transactions, the outlook is different for military-grade e-threats the size and complexity of Stuxnet, Duqu or Flamer.
Malware specializing in cyber-espionage rarely relies on the local connection to the Internet to siphon data outside of the perimeter. That approach would likely trigger firewall alerts; the huge amount of data sent to the C & C server is also likely to be visible to packet inspection applications such as Wireshark, which will compromise the operation. More likely, the attackers use an employee`s removable device as transportation between the isolated network and an unmonitored, compromised workstation at the employee`s home, for instance.
Not all malware is tailored for espionage and persistence, but is rather focused on delivering a payload or fulfilling a mission. This was the case of Stuxnet, world`s first piece of malware that was tailored to subvert an industrial system to compromise the production process at the Natanz-based uranium enrichment facility in Iran. The e-threat was particularly designed to seize control the Siemens Simatic WinCC SCADA applications controlling centrifuge machines and did not affect computers or networks that did not meet specific architecture requirements.
Conclusion
Isolated networks are the ultimate fortresses, but they are penetrable. The ecosystem is as safe as its weakest link: the human user, be it employee, system or network administrator.
The Stuxnet and Flamer incidents have demonstrated that even the most secured networks are no match for cyber-weapons, instruments designed to go where no piece of malware has gone before. These instruments, who likely share the same origin, prove that highly-skilled cyber-criminal groups can always take the game one step further and bring more and more sophisticated threats to outsmart defense mechanisms.
[1] Jeremy Faircloth, Penetration Tester’s Open Source Toolkit, third edition ” Elsevier, 2011
[2] Bogdan Botezatu, FLAME ” The Story of Leaked Data Carried by Human Vector – http://labs.bitdefender.com/2012/06/flame-the-story-of-leaked-data-carried-by-human-vector/
[3] http://pwnieexpress.com/products/power-pwn
tags
Author

Bogdan is living his second childhood at Bitdefender as director of threat research.
View all postsRight now Top posts
Start Cyber Resilience and Don’t Be an April Fool This Spring and Beyond
April 01, 2024
Spam trends of the week: Cybercrooks phish for QuickBooks, American Express and banking accounts
November 28, 2023
3 in 5 travel-themed spam emails are scams, Bitdefender Antispam Lab warns
August 10, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks