Yes, you should update your iPhone to iOS 12.1, but its lock screen is *still* unsafe
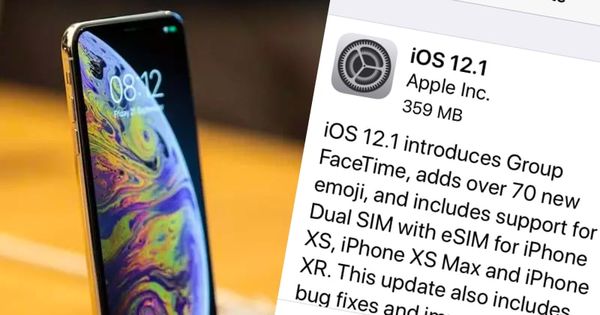
Apple has released its first major update to iOS 12 – iOS 12.1 – bringing a host of new features to iPhones and iPads including dual SIM support, Group Facetime, and for those who needed more of them in their life – 70 new emoji.
Apple is less keen to brag about the security fixes included in iOS 12.1, which include patches for vulnerabilities that could be exploited by maliciously crafted webpages and S/MIME messages, as well as a way to access photos and notes on a locked device.
That last problem was uncovered in late September by YouTuber Jose Rodriguez, who has a long track history of uncovering vulnerabilities in iOS, and demonstrating on his “videosdebarraquito” channel his convoluted methods of accessing private data held on iPhones and iPads.
Now, within minutes of Apple rolling out its latest iOS 12.1 update, Rodriguez has done it again – releasing a brand new video video showing yet again just how an iPhone or iPad’s lock screen can be bypassed to see the phone’s complete contact list.
In the video, Rodriguez demonstrates how the passcode bypass bug appears to have been introduced by the new Group Facetime feature. The first step of bypassing the lock screen is to either first receive a phone call or asking Siri to make one on your behalf, and then changing the call to a Facetime conversation.
Once the call has switched to FaceTime, it is possible to access an iPhone’s full list of contacts by tapping “Add Person” even though the device is locked. Furthermore, even more details on contacts is available using iOS’s 3D Touch feature.
It does seem as though this particular bypass is comparatively simple, especially when compared to Rodriguez’s last discovery, which required a convoluted 37 steps to worm its way past a locked iPhone’s passcode check.
Maybe Apple should offer Rodriguez a job testing upcoming versions of their iOS operating system to see if he can find a way to break in. They would certainly find it less embarrassing to learn about these flaws before the software shipped.
If such privacy flaws concern you then my best recommendation is for you to follow the same advice I gave after Rodriguez last announced an iOS lock screen bypass:
Permanently disable Siri on your lock screen. Time and time again, Siri has been found to be at the root of many of Apple’s problems when it comes to securing its mobile devices from unauthorised access.
If you care about security, you’ll disable Siri on the lock screen by going to Settings / Touch ID & Passcode, scroll down to the “Allow access when locked” section and ensuring that the feature is disabled.

Ultimately it’s your decision. Having Siri accessible via your lock screen may sometimes be convenient, but it is also a weak point in your iPhone or iPad’s security.
tags
Author
Graham Cluley is an award-winning security blogger, researcher and public speaker. He has been working in the computer security industry since the early 1990s.
View all postsRight now Top posts
Start Cyber Resilience and Don’t Be an April Fool This Spring and Beyond
April 01, 2024
Spam trends of the week: Cybercrooks phish for QuickBooks, American Express and banking accounts
November 28, 2023
3 in 5 travel-themed spam emails are scams, Bitdefender Antispam Lab warns
August 10, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








